
In today’s chip business, one increasingly common market model involves an original equipment manufacturer (OEM) buying microcontrollers from a chip supplier and then engaging an independent design house (IDH) to develop custom embedded software (which constitutes intellectual property or IP) for the chips used in the end product.
The OEM pays royalties to the IDH depending on the volume of end products that are using the IP. The OEM further engages an external programmer house to program the chips with the IP (Figure 1).
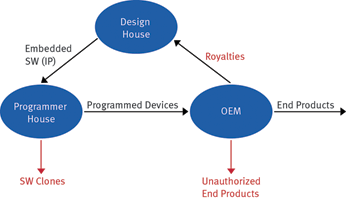
Such a model carries some risks to the OEM and the IDH. For example, the IP could be leaked through grey channels to a pirate production plant and used to produce software clones. Also, since the volume of end product is not visible to the IDH, a less fair-minded OEM may attempt to pay less royalties by under-declaring the IP usage.
Infineon’s XMC1000 microcontroller family addresses such risks by offering an IP protection option. The IDH will be empowered with the tools to encrypt the IP based on the 128-bit key Advanced Encryption Standard (AES) and the resulting encrypted IP can only be downloaded into authorised devices, where it will get decrypted and programmed into the devices’ Flash memory.
This ensures that the IP is always transported in its encrypted form until it is downloaded into the device. The IDH will now also have the means to keep track of the number of end products that would be using the IP.
Building blocks
The IP protection scheme requires three basic building blocks, as illustrated in Figure 2:
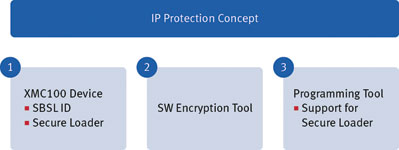
* XMC1000 device with Secure Loader.
* Software encryption tool.
* Programming tool (supporting Secure Loader).
The Secure Loader is a startup mode and feature, introduced in the XMC1000, to process 128-bit AES encrypted data. Based on a defined protocol and command set, the Secure Loader is able to receive the encrypted data, decrypt the data within the device and program the data into the Flash memory.
Devices with the Secure Loader feature are grouped based on a pre-defined number of devices, termed a batch, and each batch of devices is assigned a unique identifier called SBSL ID.
The PC-based software encryption tool is used to encrypt the IP based on 128-bit key AES (IP key) and embed information to identify the SBSL ID of the target device in the final output file. The above can be performed only after the encryption tool has received the IP, IP key and SBSL ID of the target device.
The IP key is generated from an Infineon smart card interfaced to the encryption tool through a PC/SC card reader. Both the encryption tool and the smart card will be provided by Infineon to the IDH.
A programming tool supporting Secure Loader is required to interface to the target device. When connected to a device, the programming tool will send a command to read the SBSL ID from the device and based on this SBSL ID, retrieve the matching output file containing the encrypted IP. The programming tool is also used to send the command to initiate the download of encrypted data and the subsequent programming of the IP into the device.
IP protection usage flow
IP protection is initiated when the OEM provides the SBSL ID of the target devices to the IDH. Once the SBSL ID of the target devices is known, the IDH encrypts the IP using the encryption tool and delivers the final output file containing the encrypted data to the programmer house. If more than one SBSL ID is used, there will be a corresponding number of output files generated, one for each SBSL ID.
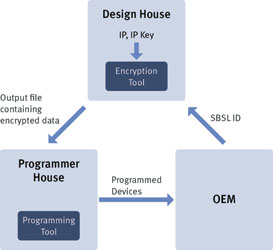
The programmer house then uses the programming tool to download the encrypted data through the Secure Loader into the target device, where it will be decrypted and programmed into the Flash memory. The programmer house must use devices that have a SBSL ID matching to the list provided by the OEM, otherwise the programming tool will flag an error and data download to the unknown device fails. The programmed devices are finally shipped to the OEM for end product assembly (Figure 3).
The discussion in this article references a market model involving an OEM, an IDH and a programmer house, but the IP protection scheme can easily be applied to other models as well.
For more information contact Davis Moodley, Infineon Technologies, +27 (0)11 706 6099, www.infineon.com
| Email: | [email protected] |
| www: | www.infineon.com |
| Articles: | More information and articles about Infineon Technologies |
© Technews Publishing (Pty) Ltd | All Rights Reserved